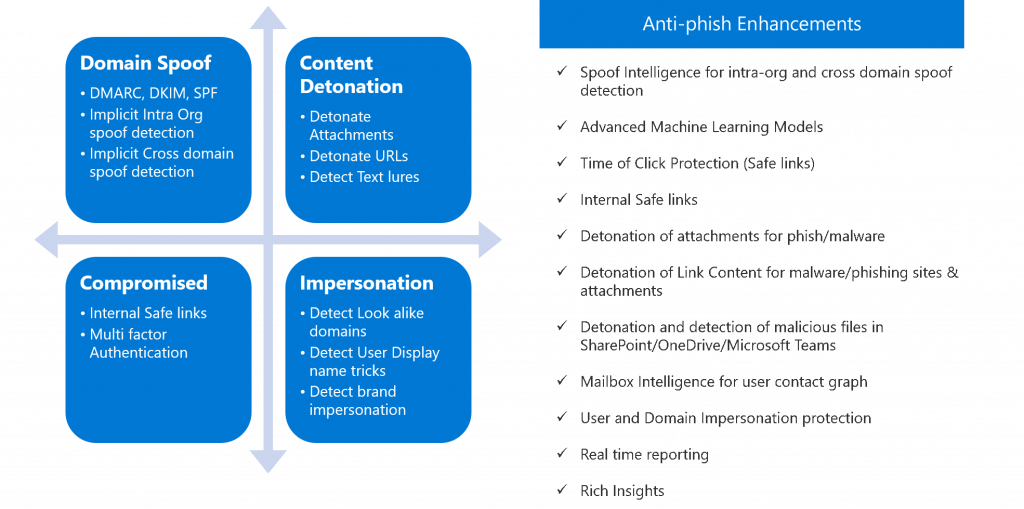
Microsoft has figured out how to shut down phishing and you’ll see that we’ve been making updates to the configuration of your services to implement these changes. The main component is called ATP (Advanced Threat Protection) but there are also configuration points like attachment blocking, country blocking, executable content blocking, DKIM and DMARC DNS records. All of which we are implementing and maintaining for you.
In this post I wanted to highlight some of the more advanced features that Microsoft has made available.
As you can see by the list above it takes a large number of different settings to catch phishing email. By design they are trying hard to look like legitimate email so it can be tricky. Two of the key features are the ability to verify that links in the email go to good places and don’t download malware onto your computer. Microsoft checks links against its worldwide database to see what happened when the location was visited. Key take-away on this is that you always want to wait for a couple of hours before clicking on any link that you feel you must click on. This gives time for the system to work. In general though remember that you should visit the website that the link wants you do by typing it in your browser yourself rather than clicking.
The second feature is called attachment detonation. Microsoft actively opens every attachment in a sandbox before it is delivered to you to see what it does. For example, if it claims to be a Word document then it should be a .docx file. If that file opens and then a script inside it runs to download malware files onto your computer, then they will block the file from delivery and instead a text file will replace the attachment letting you know that the email contained malware. Microsoft does not read your email or view the attachment. It’s done inside a sandbox and they simply measure the behavior trying to exit the sandbox.
Microsoft is the largest, by far, email service. The database of phish and malware that they have is therefore also the largest. This gives them the intelligence to analyze email activity. They call it the Microsoft Graph.
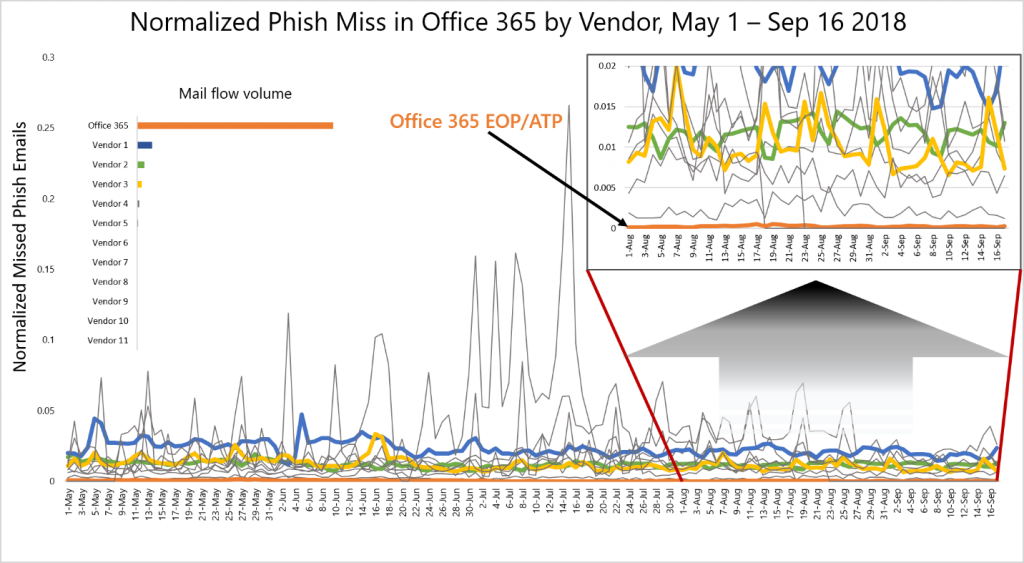
Some of these features are fairly new and as you can see above they’ve had great effect. The Orange line represents the number of successful phishing attempts and it is approaching ZERO! This is great news because Phishing is the #1 way that the bad guys have been getting malware onto networks. Since today’s malware is directly money driven via account withdrawals or ransom these new features are very important for businesses everywhere.
About Harbor Computer Services
Harbor Computer Services is an IT firm servicing Southeastern Michigan. We work exclusively under contract with our clients to provide technology direction and either become the IT department or provide assistance to the internal IT they already have. We have won many awards for our work over the years, including the worldwide Microsoft Partner of the Year in 2010. We’re the smallest firm to have ever won this most prestigious award. Most recently we were recognized as one of the top 20 visionaries in small business IT by ChannelPro Magazine (2015). And in 2016 as the top Michigan IT firm for Manufacturing. There are a few simple things that make Harbor Computer Services the best choice for your business. •We are Professionals •We are Responsible •We are Concerned About The Success of Your Business