We’ve touched on the topic of Spoofing and Phishing several times already, but it’s an extremely important topic that deserves to be repeated.
Training Videos
This week many of our clients received a training video this week that gave an introduction to Phishing, a form of Spoofing. This video gave it’s viewers an overall idea of several different types of phishing scams that they may come across.
If you received an email from Harbor about this training, please take it ASAP and encourage all of your users to do the same. It is extremely valuable.
What is Spoofing?
Spoofing is the act of fraudulently impersonating a trusted source.
Spoofing can come in the form of emails, phone calls, websites, text messages, or other technical forms.
What is Phishing?
Phishing is a form of spoofing. Phishing scams usually provide a link to a bogus website where the user is required to enter sensitive account information. The goal of the bad guys conducting the phishing scam is to obtain your personal information, which could be addresses, social security numbers, banking information and so on.
A Spoofing Example
Also occurring this week, I was alerted that one of our clients received a spoofing email. This email claimed to be from the CEO of the company, asking the end-user to purchase some gift cards. Luckily, the user questioned the legitimacy of this email and informed me and the rest of the company.
Below is a copy of that email. The name next to From was the name of the CEO of the company. The email address was not the CEO’s email address.
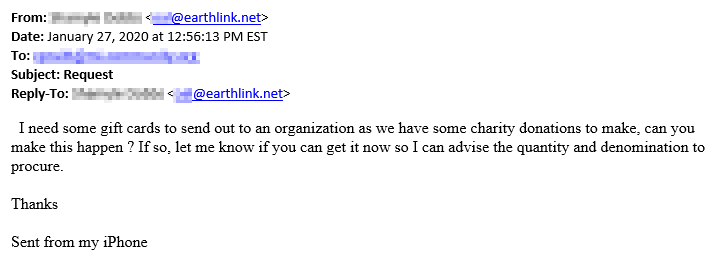
In this case, the email address was a dead giveaway! That is not always the case.
Rules for Keeping Safe from Spoofing
- Watch for poor or inconsistent grammar, unusual sentence structure, and poor spelling. Spoofing emails and phone calls often come from other countries.
- Double-check the email address or website address. Often an email or web address is spoofed by making subtle changes in the address.
Facebook.com or Facedook.com? You have to be paying attention to catch it!
- Never click on email links. If it is an email with a link to access an account of some sort, go straight to the website instead.
- If you receive a questionable communication, pick up the phone and call direct. Ask if they tried to contact you.
- Don’t take phone calls and text messages at face value. Question the legitimacy, especially if they are requesting personal information or company information.
- If it looks suspicious. It probably is. Trust your gut!
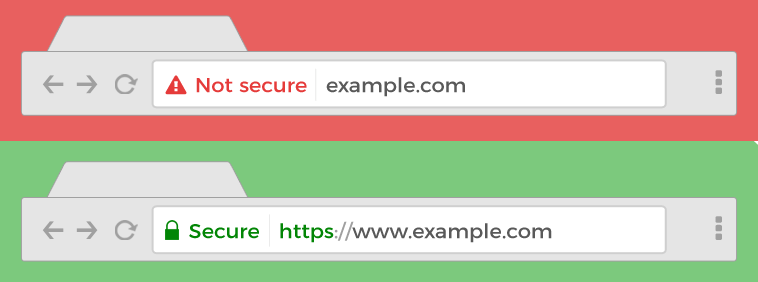
- Avoid websites that are not secure. The web address should begin with https, instead of http. The “S” stands for Security. Any website owner has to verify who they are before gaining a certificate to allow their site to be secure.
NEVER enter personal information into a website that does not begin with Https!
- Use multi-factor authentication whenever possible. This gives that added layer of security in determining your identity.
- Provide training to your employees!
Your users are the most important safeguard against security breaches. Knowledge is Power!
Harbor Computer Services offers training to all of our clients on a range of topics, including Security. Don’t hesitate to contact us!
About Harbor Computer Services
Harbor Computer Services is an IT firm servicing Southeastern Michigan. We work exclusively under contract with our clients to provide technology direction and either become the IT department or provide assistance to the internal IT they already have. We have won many awards for our work over the years, including the worldwide Microsoft Partner of the Year in 2010. We’re the smallest firm to have ever won this most prestigious award. Most recently we were recognized as one of the top 20 visionaries in small business IT by ChannelPro Magazine (2015). And in 2016 as the top Michigan IT firm for Manufacturing. There are a few simple things that make Harbor Computer Services the best choice for your business. •We are Professionals •We are Responsible •We are Concerned About The Success of Your Business




