There’s a great deal of interest in protecting privacy on mobile devices. This idea includes the activity on both your phone and laptops as they travel from WIFI to WIFI or operate over cellular and it’s not just for the paranoid it’s actually a security best practice. There are various ways to implement this and we’re going to have a look at the options using things that you already own, but I also have a warning for you.
Warning
Most VPN applications available in the app stores for your mobile devices are actually spy apps. Let me try to explain something that is very technical, in a hopefully clear manner.
Here’s how a VPN works.
Most people think a VPN works like the picture below. You’re on your computer or phone running a VPN app to protect the data that you’re sending and not be tracked, there’s a VPN encrypting your data and sending it to the destination app or website on the Internet. While it’s technically true, they have not told you something very important.
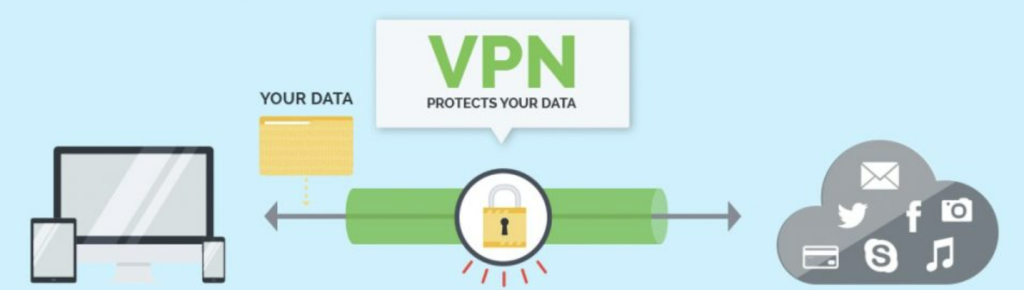
The secret to VPN and why it’s such a good way for criminals to obtain your data by providing you with the VPN app, is because your traffic is actually redirected to the VPN source, unencrypted, and then sent to its final destination. Follow the green line below and notice that it doesn’t stop at the Internet. Your internet traffic gets encrypted by the app on your device. This app sends the encrypted data to a VPN server.
Here’s where VPN security can fail. That VPN server server is owned by the company that sold or provided the VPN app to you. Your data is unencrypted by the VPN server, then sent unencrypted to its final destination. (see the dotted line below) Therefore, you must trust that VPN server completely. It can read everything you send.
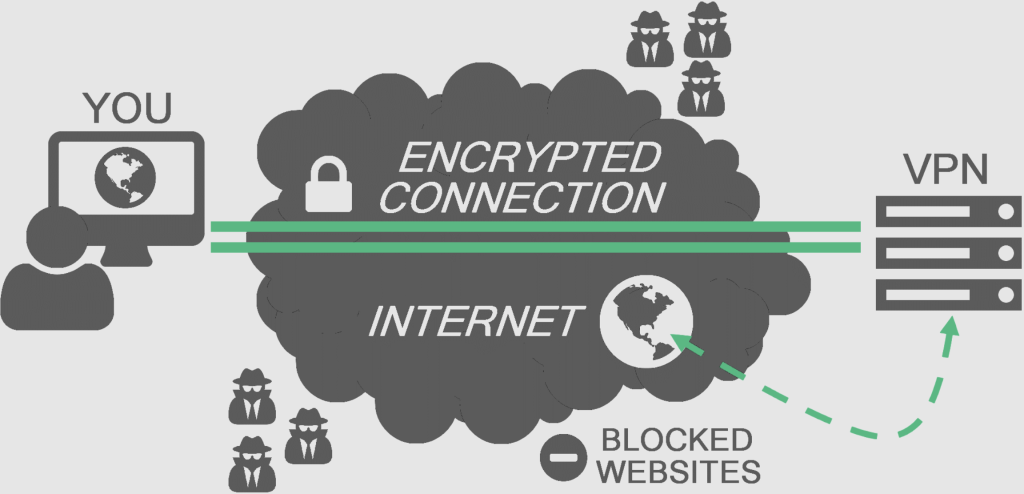
Those VPN server destinations can be in hostile countries, run by organized crime, serving up malware to you, or selling your information. This is why you must know who runs the VPN server and why you must trust them like you trust no one else, because this VPN server will know everything about you.
You should therefore avoid every free VPN app. They are nearly all scams. Here’s a list of some popular ones that are known to be bad: Hotspot shield, Betternet VPN, Touch VPN, HOLA VPN, Super VPN, Psiphon VPN, UnoTelly, EarthV PN, Mysafe VPN, Hide My Ass VPN, Ivacy VPN, Opera free VPN, Pure VPN, VPN Master, VPN Secure, WindScribe, Expatsurfer, Onavo Protect, Faceless.me, Liberty VPN, VPN Reactor, ZPN.im, Defense VPN, Dot VPN, Super VPN, One VPN, Proxy Server Pro, Cargo VPN, OK VPN, Cross VPN, Archie VPN, Hat VPN, Sfly Network Booster, OneClick VPN, Easy OVPN, VPN Free, Tiger VPNS, CyberGhost, Spotflux VPN, Globus VPN, Rocket VPN, Strong VPN, etc…
I obtained this list from publicly published lists of bad VPN’s from various articles and industry publications.
No VPN is better than a bad VPN
If you don’t have a VPN, then you might get your data sniffed but if you have a bad VPN you WILL get your data sniffed. Now for some very technical verbiage, but stay with me. Read it and realize that these apps have been studied by academics getting degrees in cyber security and cyber security professionals. From an excellent academic study of VPN apps in the Android store:
- “…75% of them use third-party tracking libraries and 82% request permissions to access sensitive resources including user accounts and text messages.”
- “…over 38% of them contain some malware presence according to VirusTotal”
- “…18% of the apps do not mention the entity hosting the terminating VPN server. [meaning they don’t tell you who is observing your data]
- Our network measurements also suggest that 16% of the analyzed apps may forward traffic through other participating users in a peer-forwarding fashion rather than using machines hosted in the cloud.” [meaning you have to trust the anyone else running the app too]
- “…18% of the VPN apps implement tunneling protocols without encryption” [meaning that they aren’t even trying to secure your information]
- “…66% of the analyzed VPN apps do not tunnel IPv6 and DNS traffic through the tunnel interface respectively due to lack of IPv6 support, misconfigurations or developer-induced errors”
- “We identified two VPN apps actively injecting JavaScript code on user’s traffic for advertisement and tracking purposes and one of them redirects e-commerce traffic to external advertising partners.”
- “Four of the analyzed VPN apps compromise users’ root-store and actively perform TLS interception...”
And in addition, they also identified that some of the popular VPN apps have endpoints hosted with home-based ISP’s. You can read that as someone’s Comcast router at home.
This is such a mess.
Is there a safe VPN?
Yes there is.
We can think of VPN’s as having two purposes. One type connects you securely to your office computer or office server. The other type encrypts all traffic regardless of the final destination and is commonly called a privacy VPN.
Let’s look at solutions for both types of VPNs.
VPN to your Office: This VPN software you probably already own. If you use the Calyptix firewall that we recommend, then the firewall generates a unique VPN package that is tied to your computer and your credentials. If a connections tries to be made from other computer or another you, then the connection will fail. This VPN tunnel is terminated at the firewall and no where else, so its trustworthy because you own the endpoint (firewall). This type of VPN client resides on a computer, not a phone. To use this VPN you turn it on when you want to connect to the office and you turn it off when you are finished.
VPN for Privacy: A privacy VPN is recommended when you are using your phone or computer on a network that you don’t trust. You might already own a Privacy VPN too. The most common example is when you’re in a public place like a coffee shop, restaurant, friends home, or other business including your client or customer. These are all places where you do not have first hand knowledge of the network health that you are joining. In that case you would want to use a privacy VPN. Privacy VPN’s are commonly used on phones and computers for general surfing and email usage. They are also used for businesses that don’t have a central office network but instead are using all cloud apps.
These privacy VPN’s are where all of the VPN troubles listed above reside. We can solve that problem by making sure that we know and trust the VPN server. If you are a business that works exclusively in cloud apps, then you should have our Firewalla firewall. One of the features of this firewall is a privacy VPN. If you work from home, this can be installed in your home too. We trust this, because we know where the firewall is located and therefore where your data is being decrypted. This VPN app will be installed on your computer and on your phone and it will be running at all times.
Another option for privacy VPN capabilities is Microsoft Defender. The Defender app is now included for all Microsoft 365 Business Premium subscribers and can be used on devices the business owns as well as provided to those that it does not own as a benefit. The only requirement for devices, like home computers and personal phones, is that they are running the Microsoft authenticator app as well as the Microsoft Defender app. Neither app exposes the content or destination of the data being transmitted. All is does is scan the destination against known privacy, malware and known bad sites and then the data is transmitted normally from your device. This means that you are your own VPN destination and of course you trust yourself.
Our advice
In short, if you downloaded a VPN app to your phone or computer, speak up now and probably uninstall it now. Let us help you get setup with a legitimate safe VPN service. You probably already own one.
Harbor Computer Services is an IT firm servicing Southeastern Michigan and beyond. We work exclusively under contract with our clients to provide technology direction and either become the IT department or provide assistance to the internal IT they already have. We win awards! Recently we were recognized in the gratitude category for our corporate culture by dBusiness magazine.
There are a few simple things that make Harbor Computer Services the best choice for your business. •We are Professionals •We are Responsible •We care about your business