$26 Billion dollars worldwide since 2016. That’s not a very long time to generate that kind of under the table money. The way to make that kind of money is through something generically called Business Email Compromise. It’s actually a lot more specific than it sounds.
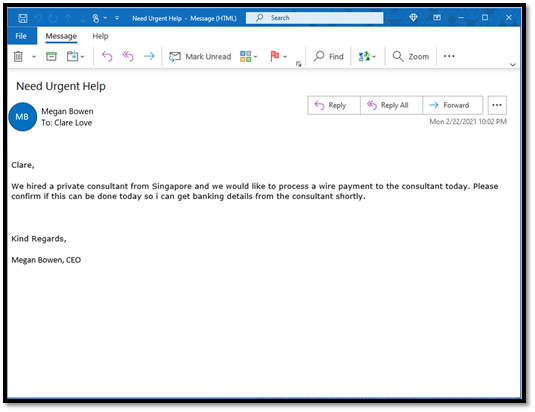
- the attacker uses the Display Name feature to hide the real from address
- the attacker uses “look alike” domain naming harborcornputerservices.net instead of harborcomputerservices.net
- the attacker uses domain forgery, which is a completely different domain but then tells is to view as your domain so you think it’s an internal email
I prefer the term, criminal, to attacker since their goal is to cause you to give up your money. A stick up from a distance if you will.
How we protect from this
Remembering that nothing is 100% and we can’t carry your liability, we don’t write the software, we aren’t there reviewing every click you make and all of those legal things. Here are the features of 365 that we implement to protect you from these types of attacks.
Collectively the features are called Mailbox Intelligence and when we enable that intelligence, we’re asking the system to build a profile of your email patterns and then to consider those patterns within it and alert you when something has come in that is outside of that pattern.
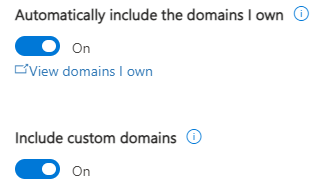
First, we tell it which email domains to pay special attention to. Of course, we want your domain, but we can also include other people’s domains. In that custom domain category, we’ll include key customers like those that you might get money transfer requests from, those connected to BIG contracts, so the criminals don’t use you to get to that larger corporation or government entity. We can even include those where you know they’ve had a compromise. Small businesses are often used as a steppingstone to get to Tier 1 suppliers and government agencies.
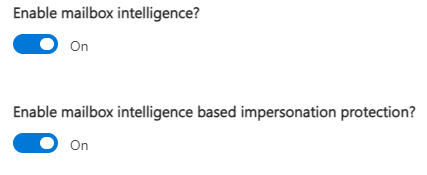
Next, we turn on the mailbox intelligence and impersonation protection. After we do that, then we tell it which users we want to have this extra layer of protection on. Meaning which users is it going to collect enough information on, to be able to understand when an email is out of the norm for that person’s email pattern.
Finally, because we’re asking a faceless artificial intelligence to make email decisions for us and we’re implementing these “extra” security measures we know that they’ll also have a small impact on the overzealous side. Meaning some email will end up in quarantine that should have been delivered. For that, we have allow listing. Allow listing is a bit of a manual process and it can be dangerous. Because we’re telling the system to override and deliver the message anyway.
Allow listing can be required because of the bad reputation of the ISP, the domain or the email user causes these protections to mark the sender as unsafe. But in those cases, you’re also agreeing to take on the risk of getting mail from that risky location or person or ISP. Often there’s no choice but it is a security awareness issue. When you add to the allow list, know that just because that email is now delivered to your inbox instead of making a stop in quarantine first, doesn’t necessarily make life suddenly wonderful. What it actually does is put more responsibility for risk on the person receiving the email to their inbox.
That’s a quick summary of something that we do on our end that you hopefully never see to protect you from email impersonation attacks by criminals.
About Harbor Computer Services
Harbor Computer Services is an IT firm servicing small businesses. We work exclusively under contract with our clients to provide technology direction and either become the IT department or provide assistance to the internal IT they already have. We have won many awards for our work over the years, including the worldwide Microsoft Partner of the Year in 2010. In 2020, we were recognized as one of the top MSP’s by ChannelFutures coming in at #40 worldwide. And in 2016 as the top Michigan IT firm for Manufacturing. There are a few simple things that make Harbor Computer Services the best choice for your business. •We are Professionals •We are Responsible •We care about your business




