I realize how that subject line reads so just so no one panics these are two separate topics completely unrelated.
Equus: While travelling recently in California I had the pleasure of taking my Third Tier team to be the speakers for the October SMBTechFest and since I was in the LA area I paid a visit to the Equus manufacturing facility. This is where complex custom server configurations, OEM machines and Laptops are built. They build $4.5 million dollars of equipment each week. This location is the largest of their build centers. I was given the tour by the facilities manager and national sales manager; it was very impressive. Not only for the method but for the results. In a year they have less than $1000 inventory loss and .01 failure. That is amazing considering how the value of computer equipment plummets with every passing day. Besides the equipment that we order from them, Equus also designed and builds all of the equipment for NetFlix. We saw machines being loaded with the entire NetFlix library. Now that’s some data transfer! Next time you rent a movie from NetFlix remember that it is being loaded from Equus equipment just like in your office. I witnessed the LEAN manufacturing process and how staff changes jobs to maximize efficiency at different times of day. As an ESOP the employees own this company and the value of their stock has doubled every year and it might even triple this year! Equus remains a strong American manufacturing company with a commitment to small and medium business. I’m happier than ever that we work with them to provide you with the best computer products available.
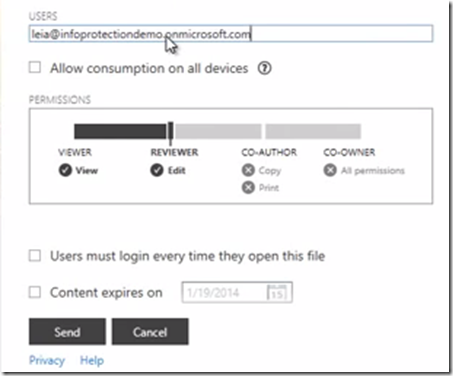
Cryptolocker: Cryptolocker continues to rage through the land. This virus arrives as an attachment and then proceeds to encrypt any files that the person logged into that computer has access to in the network. Anti-Virus software does not catch it because its behavior isn’t unusual in any way. It installs like normal software and it uses only the rights that the logged in person already has. This means it doesn’t break any rules. While not breaking any rules, it is still an attachment and it is still software. Using information provided on its behavior by bleepingcomputer.com we were then able to develop some precautions. We have done this via a new Group Policy deployment to your computers and a change in the backup permission settings. In addition, if you are a Harbor Secure Cloud subscriber then the attachments themselves are also blocked from your corporate email account. While nothing is 100% we believe that we’ve taken very good precaution to protect you.
I then took our procedures, the policies and an accompanying paper written by a member of my staff at Third Tier and put them together into what I called the Cryptolocker Prevention Kit and published it on my technical blog. It has been downloaded between 800-1000 times per day by other IT professionals around the world since. It has also been highlighted as THE solution by GRC, CNBC, SpiceWorks, Redmond Magazine and other prominent news sources. Unfortunately it has also been copied and published by others claiming authorship. The funny thing is that the policy puts a link to Harbor on the desktop. I’ve been getting some interesting calls and email from people that got the Kit from a stolen source and are now wondering how they got Harbor on their desktop! They lack the document that explains how to put their own information into the policy before deploying it since they obtained our Kit from another source. The moral there is to never deal with pirates only the original source.
We freely shared this information with our peers in the IT industry because we felt a need to do so. There was a lot of fear and uncertainty and since we had what we thought was a good solution we shared it. Better that more businesses get protected from disaster or extortion than fewer.
Next week I will be attending Microsoft MVP Summit in Redmond, where I’ll have many opportunities to provide input into new technologies being developed there.
-Amy